Blockchain is a revolutionary technology that serves as a decentralized and distributed digital ledger. It functions as a transparent and secure system for recording and verifying transactions across multiple computers or nodes. Unlike traditional centralized systems, where data is stored and controlled by a single entity, blockchain operates on a network of interconnected nodes, each maintaining a copy of the entire blockchain. Cybersecurity is a vital field dedicated to safeguarding computer systems, networks, and data from unauthorized access, malicious activities, and potential harm. With the increasing reliance on technology in various aspects of our lives, including finance, cybersecurity has become crucial to protect sensitive information and ensure the smooth operation of digital infrastructure. The primary objective of cybersecurity is to establish a robust defense against cyber threats and vulnerabilities. These threats can come in various forms, such as hackers attempting to breach systems, malware infecting networks, or phishing attacks targeting individuals to gain unauthorized access to their accounts or personal data. Blockchain operates on a decentralized network of nodes, distributing data across multiple computers. Each node maintains a complete copy of the blockchain, consisting of transactional blocks. This distributed ledger promotes transparency and trust. Consensus algorithms like Proof of Work or Proof of Stake ensure agreement on transaction validity. Cryptographic techniques secure the blockchain. Encryption protects transaction data from unauthorized access, while digital signatures verify integrity and authenticity. Cryptographic hashing assigns a unique identifier to each block, acting as a digital fingerprint. Tampering attempts trigger hash value changes, alerting the network. Blockchain's burstiness and transparency stem from its decentralized structure, consensus mechanisms, and cryptographic security measures. The key components of a blockchain system are essential building blocks that contribute to its functionality, security, and trustworthiness. These components work in harmony to establish a robust and reliable blockchain network. Here are the key components: Consensus mechanisms ensure that all nodes in the blockchain network agree on the validity and order of transactions. Various consensus algorithms, such as Proof of Work (PoW) or Proof of Stake (PoS), are used to achieve consensus. These mechanisms prevent double-spending and maintain the integrity of the blockchain by ensuring agreement among participants. Cryptographic hashing is a process where data is transformed into a fixed-size, unique digital fingerprint called a hash. Each block in the blockchain contains a hash that represents the data within the block. Hashing algorithms, such as SHA-256 (Secure Hash Algorithm 256-bit), are used to generate these unique identifiers. Hashing ensures the integrity of the data by detecting any tampering attempts. Even a small change in the data will result in a completely different hash value. Digital signatures are used to verify the authenticity and integrity of transactions. They provide a way for participants to prove that a transaction was created by the rightful owner and has not been tampered with. Digital signatures are created using cryptographic algorithms and are unique to each transaction. They rely on public-private key pairs, where the private key is used to sign the transaction, and the corresponding public key is used to verify the signature. Blockchain operates on a peer-to-peer network, where each node maintains a copy of the entire blockchain. This decentralized architecture eliminates the need for a central authority and enables direct interaction between participants. Peer-to-peer networking ensures redundancy, fault tolerance, and resiliency. It allows for the propagation of transactions and blocks across the network, ensuring that all participants have the same view of the blockchain. The integration of cybersecurity measures is essential to ensure the robustness and resilience of blockchain systems. By implementing appropriate security measures, blockchain networks can enhance the protection of sensitive data, prevent unauthorized access, and mitigate the risks associated with cyber threats. Here are key cybersecurity measures that can be integrated into blockchain: Proper key management is crucial for maintaining the security of blockchain systems. Strong cryptographic keys, including private keys used for digital signatures, must be generated and stored securely. Measures such as using hardware wallets or secure key storage solutions can be implemented to safeguard private keys from unauthorized access or theft. Encryption plays a vital role in protecting data confidentiality. Data at rest, such as stored transactions or user information, can be encrypted to ensure that even if unauthorized access occurs, the data remains unintelligible. Additionally, data transmitted between nodes or across networks should be encrypted to prevent interception and tampering. Implementing strong access controls helps prevent unauthorized access to blockchain networks and systems. This includes authentication mechanisms, such as multi-factor authentication, that ensure only authorized individuals can access sensitive information or perform critical operations within the blockchain ecosystem. Role-based access controls can be implemented to grant appropriate privileges based on user roles and responsibilities. Regular security audits and assessments are crucial to identify vulnerabilities and assess the overall security posture of the blockchain system. These audits involve examining the network infrastructure, analyzing code quality, conducting penetration testing, and assessing compliance with security standards and best practices. Through security audits, organizations can proactively identify and address security weaknesses and potential entry points for attackers. Having a well-defined incident response plan is essential to minimize the impact of security incidents and facilitate quick recovery. This plan should outline the steps to be taken in the event of a security breach, including incident detection, containment, investigation, recovery, and communication. By promptly responding to security incidents and having a recovery plan in place, organizations can mitigate the damage caused by potential breaches. Continuous monitoring of blockchain networks helps detect and respond to potential security threats in real time. This involves monitoring network traffic, analyzing system logs, and using intrusion detection and prevention systems. Additionally, staying informed about emerging threats and vulnerabilities through threat intelligence sources ensures that organizations can proactively address new and evolving cyber threats. One of the key benefits of blockchain technology in finance is the increased transparency it offers. Blockchain allows all participants in the network to view and verify transactions, creating a transparent and auditable record of financial activities. This transparency enhances trust among financial institutions, businesses, and customers as it eliminates the need to rely on centralized authorities or intermediaries for verification. Instead, participants can independently verify transaction details, ensuring transparency and reducing the risk of fraudulent activities. Blockchain's immutability ensures the integrity of financial transactions. Once a transaction is recorded on the blockchain and added to a block, it becomes nearly impossible to alter or tamper with. The decentralized nature of blockchain and the consensus mechanisms employed make it extremely difficult for any malicious actor to modify or manipulate the transaction records. This feature reduces the risk of fraud and unauthorized changes, providing a reliable and tamper-resistant record of ownership and transaction history. Blockchain utilizes cryptographic techniques to secure data and protect it from unauthorized access. Transactions stored on the blockchain are encrypted, ensuring confidentiality and privacy. Moreover, participants have control over their personal information and can choose what information to share or keep private. This reduces the reliance on centralized authorities or third parties for data management and storage, enhancing data security and privacy for individuals and businesses. Blockchain technology eliminates the need for intermediaries and manual reconciliations in financial processes, resulting in streamlined and efficient operations. Traditionally, financial transactions involve multiple intermediaries and time-consuming reconciliation processes. With blockchain, transactions can be executed directly between parties, reducing costs, minimizing delays, and speeding up settlement times. Smart contracts, which are self-executing agreements coded on the blockchain, automate and enforce the terms of transactions, further enhancing efficiency and reducing the need for manual intervention. Blockchain's decentralized nature removes the reliance on intermediaries, such as banks or clearinghouses, for financial transactions. This decentralization reduces costs associated with intermediaries, eliminates single points of failure, and enhances the overall resilience of the financial ecosystem. Transactions can be conducted directly between participants, reducing delays and complexities introduced by intermediaries. Additionally, decentralization promotes financial inclusion by providing access to financial services for individuals and businesses in underserved or unbanked areas, bypassing the need for traditional financial institutions. Scalability is a significant challenge for blockchain networks as they expand in size and usage. Traditional blockchains, like Bitcoin and Ethereum, face limitations in transaction throughput and latency due to the consensus mechanisms and block size restrictions. To address this challenge, innovative solutions are being explored. Off-chain transactions, such as payment channels or sidechains, enable parties to conduct transactions off the main blockchain, reducing the overall load. Layer-two scaling techniques, like the Lightning Network, facilitate faster and more scalable transactions by leveraging the underlying blockchain's security. Blockchain-based financial systems must adhere to existing regulatory frameworks and legal requirements. However, the decentralized and borderless nature of blockchain presents challenges in compliance. Striking a balance between regulatory compliance and the potential of blockchain technology necessitates collaboration between regulators and industry participants. Governments and regulatory bodies are working to understand and adapt regulations to accommodate blockchain innovations, creating regulatory sandboxes and fostering dialogue to address legal implications such as privacy, data protection, and anti-money laundering. While blockchain technology enhances security, it is not immune to cybersecurity risks. Cyber attacks such as 51% attacks, DDoS attacks, or smart contract vulnerabilities can pose threats to blockchain networks. Robust cybersecurity measures are essential to mitigate these risks. This includes implementing strong encryption techniques, secure coding practices, conducting regular vulnerability assessments, and implementing incident response plans. Collaboration among blockchain developers, security experts, and the wider cybersecurity community is crucial to identify and address emerging threats and vulnerabilities. The energy consumption associated with some blockchain networks, particularly those utilizing Proof of Work consensus mechanisms, raises concerns about sustainability. As blockchain networks grow, the computational power required for consensus and mining increases, leading to high energy consumption. Efforts are being made to address this challenge by developing energy-efficient consensus mechanisms like Proof of Stake and exploring alternative energy sources for mining operations. Furthermore, organizations are working towards improving the overall energy efficiency of blockchain networks to ensure their long-term sustainability and minimize their environmental impact. Blockchain and cybersecurity intersect in the realm of finance, offering numerous benefits. Blockchain serves as a transparent and secure decentralized ledger, increasing transparency, trust, and immutability. It utilizes cryptographic techniques such as encryption and digital signatures to protect data integrity and privacy. Consensus mechanisms ensure agreement on transactions, while peer-to-peer networking ensures redundancy and fault tolerance. By integrating cybersecurity measures, organizations can enhance blockchain security, including secure key management, data encryption, access controls, security audits, incident response planning, and ongoing monitoring. In finance, blockchain fosters transparency, enhances security, streamlines processes, and eliminates intermediaries, while challenges include scalability, regulatory compliance, cybersecurity risks, and energy consumption. Despite these challenges, the integration of blockchain and cybersecurity holds significant potential for revolutionizing finance and strengthening the digital infrastructure.What Is Blockchain and Cybersecurity?
Definition of Blockchain
Definition of Cybersecurity
How Blockchain and Cybersecurity Work
Key Components of Blockchain
Decentralized Consensus Mechanisms
Cryptographic Hashing
Digital Signatures
Peer-to-Peer Networking
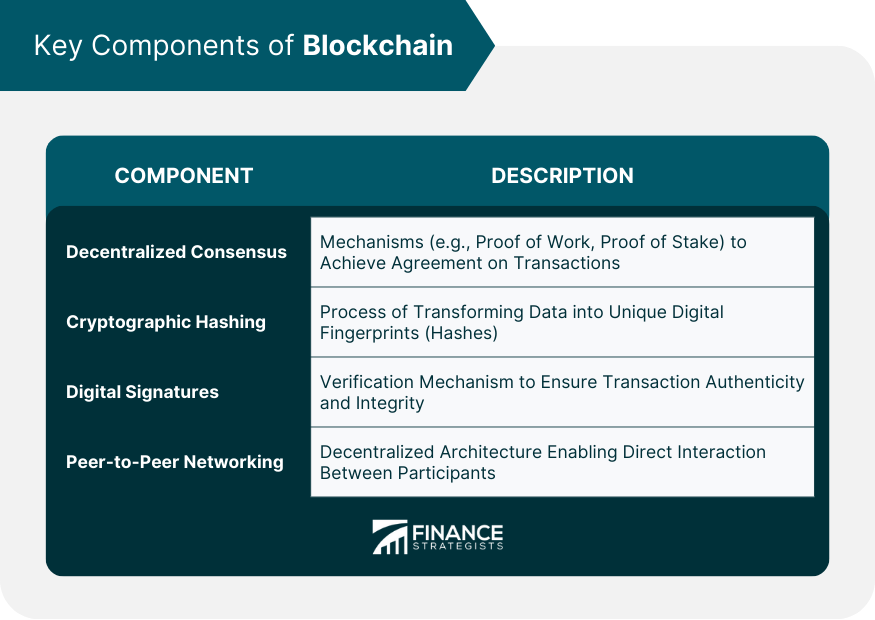
Integration of Cybersecurity Measures in Blockchain
Secure Key Management
Encryption of Data at Rest and in Transit
Access Controls
Regular Security Audits
Incident Response and Recovery Planning
Ongoing Monitoring and Threat Intelligence
Benefits and Advantages of Blockchain and Cybersecurity in Finance
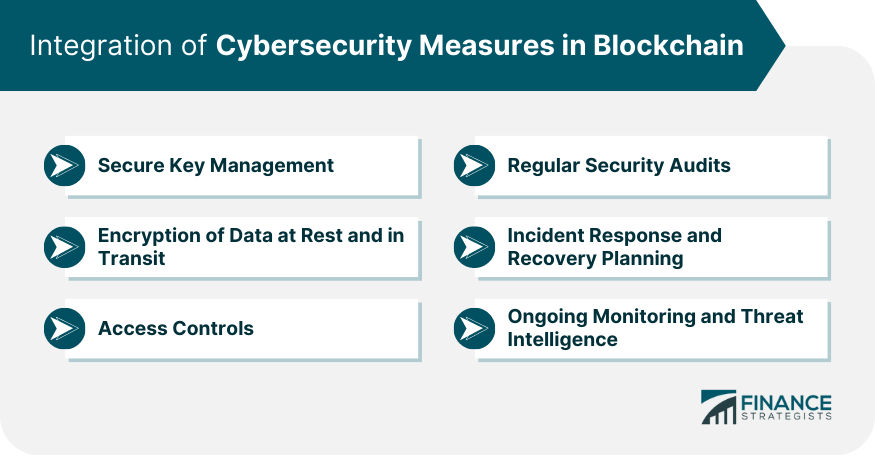
Increased Transparency and Trust
Immutable and Tamper-Resistant Transactions
Enhanced Data Security and Privacy
Streamlined and Efficient Processes
Decentralization and Elimination of Intermediaries
Challenges in Blockchain and Cybersecurity for Finance
Scalability and Performance Considerations
Regulatory Compliance and Legal Implications
Mitigating Cybersecurity Risks and Attacks
Energy Efficiency and Sustainability in Blockchain
Conclusion
Blockchain and Cybersecurity FAQs
Blockchain enhances cybersecurity by utilizing cryptographic techniques to secure data, ensuring confidentiality, integrity, and authenticity. It creates a transparent and tamper-resistant record of transactions, reducing the risk of fraud and unauthorized changes.
While blockchain technology enhances security, it is not a foolproof solution against all cyber attacks. It mitigates certain risks by decentralizing control, employing consensus mechanisms, and utilizing encryption. However, organizations must still implement robust cybersecurity measures to protect against evolving threats.
Cryptography plays a fundamental role in blockchain by providing secure encryption, hashing, and digital signatures. It ensures the confidentiality of data, verifies the integrity of transactions, and establishes the authenticity of participants, enhancing the security of blockchain networks.
Blockchain improves trust in financial transactions by providing transparency and immutability. All participants can independently verify transactions, reducing reliance on intermediaries. The decentralized and tamper-resistant nature of blockchain enhances trust by ensuring a transparent and auditable record of ownership and transaction history.
While blockchain technology offers enhanced security, it is not entirely immune to cybersecurity risks. Threats include 51% attacks, DDoS attacks, smart contract vulnerabilities, and private key compromises. Implementing strong encryption, secure coding practices, regular vulnerability assessments, and incident response plans are essential to mitigate these risks.
True Tamplin is a published author, public speaker, CEO of UpDigital, and founder of Finance Strategists.
True is a Certified Educator in Personal Finance (CEPF®), author of The Handy Financial Ratios Guide, a member of the Society for Advancing Business Editing and Writing, contributes to his financial education site, Finance Strategists, and has spoken to various financial communities such as the CFA Institute, as well as university students like his Alma mater, Biola University, where he received a bachelor of science in business and data analytics.
To learn more about True, visit his personal website or view his author profiles on Amazon, Nasdaq and Forbes.